This article by Alberto G. Alexander, Ph.D, focuses on the major components of an effective cyber risk management process. Different options for establishing a cyber risk framework are presented and best practices for cyber risk management are suggested.
Introduction
Cyber risk management is the practice of prioritizing cyber security defensive measures based on the potential adverse impact of the threats they’re designed to address. Establishing a risk management approach to cyber security investment acknowledges that no organization can completely eliminate every system vulnerability or block every cyber attack. Through cyber risk management, an “organization attends first to the flaws, the threat trends, and the attacks that matter most to their business.” (Leirvik, 2021). Risk management encompasses the identification, evaluation, and prioritization of risks (defined in ISO 31000:2018 as the effect of uncertainty on objectives).
There are some concepts and definitions that need to be clarified to better understand the process of cyber risk management. Cyber needs to be understood and very well defined. “One definition of the term cyber (an abbreviation for cyber space) encompasses all digital networks required for storage, modification and communication of information,” (Antonucci, 2017). The National Institute of Standards and Technology (NIST) defines cyber space as “a global domain within the information environment consisting of the interdependent network of information systems infrastructures including the Internet, telecommunications networks, computer systems, and embedded processors and controllers”.
Cyber risks can result in serious organizational impacts, leading, for example, to business interruption or major reputational damage. This may consequently cause even larger losses than traditional business and industrial risks.
The term cyber threat generally applies to any vector that can be exploited in order to breach security, cause damage to the organization, or exfiltrate data.
In figure one, the threat categories facing organizations are presented. Following this there is a brief description of each category.
Figure one: Threat categories facing organizations
- Adversarial threats – including third-party vendors, insider threats, trusted insiders, established hacker collectives, privileged insiders, ad hoc groups, suppliers, corporate espionage, and nation-states. This category also includes malicious software (malware) created by any of these entities. Large organizations mitigate these threats by establishing a security operations center (SOC) with trained security staff and specialized tooling.
- Natural disasters – hurricanes, floods, earthquakes, fire, and lightning can cause as much damage as a malicious cyber attacker. A natural disaster can result in loss of data, disruption of services, and the destruction of an organization’s physical or digital resources. The threat of natural disaster can be minimized by distributing an organization’s operations over multiple physical sites or using distributed cloud resources.
- System failure – when a system fails, it may cause data loss and also lead to a disruption in business continuity. Make sure that your most critical systems are running on high-quality equipment, have redundancy in place to ensure high availability, are backed up, and your providers offer timely support.
- Human error – any user may accidentally download malware or get tricked by social engineering schemes like phishing campaigns. A storage misconfiguration may expose sensitive data. To prevent and mitigate these threats, firms should establish an employee training program and enforce strong security controls. For example, use password managers and monitor critical systems for misconfigurations.
The most important threat vectors that affect the majority of organizations are:
- Unauthorized access – may be the result of malicious attackers, malware, and employee error.
- Misuse of information by authorized users – an insider threat may misuse information by altering, deleting, or using data without authorization.
- Data leaks – threat actors or cloud misconfiguration may lead to leaks of personally identifiable information (PII) and other types of sensitive data.
- Loss of data – poorly configured replication and backup processes may lead to data loss or accidental deletion.
- Service disruption – downtime may cause reputational damages and revenue losses. It may be accidental, or the result of a denial of service (DoS) attack.
Organizations need to be able to appropriately identify and mitigate risks, and then enforce the application of a risk management framework which best suits its needs and organizational cultural aspects.
Cyber risk management frameworks
There are several cyber risk management frameworks, each of which provides standards that organizations can use to identify and mitigate risks. Senior management and security leaders use these frameworks to assess and improve the security posture of the organization.
“A cyber risk management framework can help organizations effectively assess, mitigate, and monitor risks; and define security processes and procedures to address them,” (Hodson, 2019).
Here are some commonly used cyber risk management frameworks:
NIST CSF
The National Institute of Standards and Technology Cybersecurity Framework (NIST CSF) is a popular framework. The NIST CSF framework provides a comprehensive set of best practices that standardize risk management. It defines a map of activities and outcomes related to the core functions of cyber risk management – protect, detect, identify, respond, and recover.
ISO 27001
The International Organization for Standardization (ISO) has created the ISO/IEC 27001 standard in partnership with the International Electrotechnical Commission (IEC). The ISO/IEC 27001 cyber security framework offers a certifiable set of standards defined to systematically manage risks posed by information systems. Organizations can also use the ISO 31000 standard, which provides guidelines for enterprise risk management.
DoD RMF
The Department of Defense (DoD) Risk Management Framework (RMF) defines guidelines that DoD agencies use when assessing and managing cyber risks. RMF splits the cyber risk management strategy into seven key steps – prepare, categorize, select, implement, assess, authorize, and monitor.
FAIR Framework
The Factor Analysis of Information Risk (FAIR) framework is defined for the purpose of helping enterprises measure, analyze, and understand information risks. The goal is to guide enterprises through the process of making well-informed decisions when creating cyber security best practices.
PCI DSS
The Payment Card Industry Data Security Standard (PCI DSS) is an information security standard for organizations that handle branded credit cards from the major card schemes. The standard was created to increase controls around cardholder data to reduce credit card fraud.
Implications for organizations
Based on the existing frameworks and the findings and discussions in the literature, a holistic management of cyber risks appears to be vital. With the increasing importance of information and information technology for business operations, the implementation of an enterprise-wide cyber risk management process and the adaption of adequate response objectives is a necessity.
Adequate IT security measures as well as coverage by cyber insurance policies as a particular risk management tool can help to lower cyber risk exposures. Particularly, Internet-only firms and service platforms should hedge their risk positions, as in the actual case of website downtimes, revenues will drop and customers will still be able to acquire the desired goods from other firms. “Possible intangible long-term costs from such cyber incidents will therefore directly influence all lines of business and hence, in the worst case, strongly reduce market value,” (Evans,2019). Furthermore, “cyber risk management should be interpreted as a process, being subject to continuous monitoring, reviewing and improvement,” (Alexander,2016).
Finally, organizational management should be mindful that risk awareness among all stakeholders (employees, suppliers, etc.) creates a sound environment for good cyber risk management.
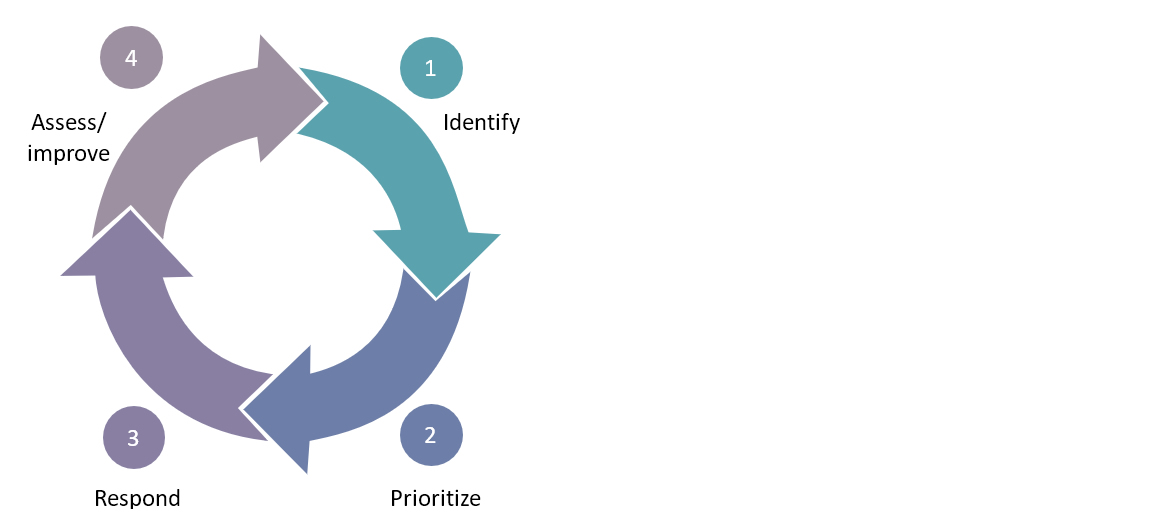
In figure two the components of risk management are depicted. It is a sequence of four steps that need to be performed.
Figure two: Components of risk management
Challenges associated with cyber risk management
Although guiding frameworks exist, a successful cyber risk management approach still represents a challenge for businesses. Such challenges partly arise from the continuous change (the continuous change of traditional business models to Internet and digitally dependent business models) and knowledge deficits (problems with the correct asset valuation/loss estimation, data insufficiencies or lack of awareness among stakeholders).
The change of traditional business models to modern, more complex and interconnected Internet-based business models affects the vulnerability of data privacy and will increasingly boost demand for cyber risk management. “The continuing digitalization of traditional business models will consequently force usage of online applications, increasing the amount of personal data online and hence expanding the potential for cyber risks,” (Hodson, 2019).
Furthermore, the current knowledge on cyber risks and risk management plays a crucial role. From a business perspective, the correct asset valuation in terms of a cyber risk management process is a key challenge for companies assessing cyber risks in general. Firms need to adequately assess their tangible and intangible assets to determine possible losses and threats. This is particularly relevant for the determination of the precise loss amount in a case of cyber incident occurrence, but also for the implementation of adequate risk response measures, as previously outlined. In this regard, firms have to understand that many IT systems (hardware and software) are mainly mass products, and thus a particularly high correlation of risks is possible, leading to potential accumulation of risks. In addition, the fast-changing technological evolution demands a “dynamic cyber risk management process, which quickly adapts to a changed cyber environment and thus cyber risk exposures,” (Leirvik, 2021).
Additionally, “the general problem of insufficient data for the proper calibration of cyber risks management (e.g., in terms of impacts from cyber threats) is strengthened by the fact that cyber incidents are often not reported, as firms fear negative effects on their shareholder value or reputational losses,” (Frohnhoefer, Pangilinan,2019). This reduces the total knowledge “base on cyber risks, and although data from operational risk databases seem to be available that also include losses from cyber risk incidents, the quantity and quality of these data appear to be insufficient to cover the breadth of cyber risk incidents,” (Antonucci, 2017).
Finally, an essential challenge for effective cyber risk management will be presented by people, as general awareness of cyber risks, i.e., its threats and consequences, seems lacking among a large proportion of IT users.
Best practices for cyber risk assessment
The following list presents a number of best practices for cyber risk assessment:
Build cyber security into the enterprise risk management framework
Fully incorporate the risk-based cyber security program into the enterprise risk management framework, which functions as the organizing principle for analyzing and classifying enterprise risks. The framework should not be used as a general guideline, but rather as the organizing principle. By framing cyber risk as a business risk, this approach makes cyber risk management more intelligible to businesses.
Identify value-creating workflows
Identify the workflows that generate the greatest business value and define their associated risks. It is important to consider the potential impact of crucial workflows because these can also pose a significant risk. For example, payment processes create value but present a business risk, as they are vulnerable to fraud and data leakage.
Make sure the cyber security team knows which processes are regarded as valuable for the organization, and define the components (data assets, tools, teams) involved in each process. This allows the firm, to apply the recommended controls. A collaborative approach involving both cyber security and business personnel is more effective than the one-sided maturity-based approach.
Prioritize cyber risks
Determine risk level based on the cost of prevention and value of information to inform risk management and mitigation procedures. High-level risks should be addressed as soon as possible, while low-level risks can be addressed down the line or accepted as a tolerated risk. If the cost of protecting an asset is higher than its value, the expense is not worthwhile unless the risk may impact business reputation.
Implement ongoing risk assessments
Perform continuous, adaptive, and actionable risk identification and assessment to keep up with evolving cyber security threats and solutions. Regularly review risk management processes to identify and remediate gaps. Cyber security teams rely on actionable insights from risk assessments to secure digital environments and assets.
Considerations for cyber risk management
There are a number of steps that organizations can take to ensure effective cyber risk management on a continuous basis. Let’s take a look at some of the most important considerations for organizations to keep in mind when overseeing their IT ecosystem:
Distribute responsibility
The burden for maintaining cyber security cannot rest exclusively on the IT or security departments. Every employee in the organization needs to be aware of potential risks and be responsible for preventing security breaches. The security plans have to take into account not just hardware and software, but also human factors. Most of the reports show that the majority of data breaches are caused by phishing.
To guard against these human-related intrusions, employees need the right tools and training to recognize malware, phishing emails, and other social engineering attacks. This is part and parcel of developing an organizational culture that supports cyber risk management.
Train employees
To implement a cyber security plan, the organization needs to establish continuous never-ending employee cyber security training, and fully train staff at all levels on the identified risks and on the procedures and systems designed to mitigate those risks. Employee training is necessary to spread and encourage a security aware culture, as well as to ensure all employees know how to use the cyber security systems and tools planned to implement.
A robust security awareness program should educate employees about corporate policies and appropriate procedures when working with IT assets and sensitive data. Employees should be trained to know exactly which types of data should not be shared over email and who to contact if they’ve discovered a security threat. Some important topics to be included in the training can include password security, safe Internet habits, clean desk policies, data management and privacy, bring-your-own-device (BYOD) policies, and more.
Share information
Putting cyber security in a silo will result in failure. Information about cyber risks need to be shared across all departments and at all levels. What the company is doing related to cyber security must be communicated to all the appropriate stakeholders, especially those involved in the company’s decision-making. You need to clearly communicate with all appropriate parties about the potential business impacts of relevant cyber risks – and then keep them aware and involved in ongoing activities.
Implement a cyber security framework
It is important to implement the appropriate cyber security framework for the company. This is typically dictated by the standards adopted by the industry.
Prioritize cyber risks
Firms do not have an infinite number of employees or an unlimited budget. Put simply, a company cannot protect against all possible cyber risks. Consequently, it is necessary to prioritize risks in terms of both probability and the level of impact, and then prioritize the security preparations accordingly.
Encourage diverse views
Too often cyber security staff and management view risk from a single viewpoint, often based on personal experience or company history. But cybercriminals seldom share this same viewpoint; malicious actors are more likely to think ‘outside the box’ and identify weak points in the system that the organization haven’t seen before or even considered. For this reason, it’s useful to encourage team members to think of and argue different points of view. This sort of diversity in thinking will help identify more risks and more possible solutions.
Emphasize speed
When a security breach or cyber attack occurs, an immediate response is required. The longer it takes to address the threat, the more damage may be done. Studies show that 56 percent of IT managers take more than 60 minutes to get information about an ongoing cyber attack. But a lot of damage can be done in an hour.
The speedy reaction must be a part of the security-forward culture. That means that organizations need to develop an early recognition of the potential risks, immediate identification of the attacks and breaches, and rapid response to security incidents. When it comes to risk containment, speed is of the essence.
Develop a risk assessment process
Risk assessment is an important part of any cyber risk management approach. The basic requirements are:
- Identify all the company’s digital assets, including all stored data and intellectual property.
- Identify all potential cyber threats, both external (hacking, attacks, ransomware, etc.) and internal (accidental file deletion, data theft, malicious current or former employees, etc.).
- Identify the impact (financial and otherwise) if any of the assets were to be stolen or damaged.
- Rank the likelihood of each potential risk occurring.
- Develop an incident response plan.
In figure two above the components of risk management are depicted. It is a sequence of four steps that need to be performed.
Develop an incident response plan focusing on the priority of risks that have previously been identified. The organization needs to know what to do when a threat is detected – and who needs to do it. This plan should be codified so that even if an incident occurs after people leave the company, the team currently in place will have a roadmap for how to respond.
Be attentive to the threat environment
Cybercriminals continue to leverage information gathered from public sources, such as LinkedIn or Facebook, to launch sophisticated ‘whaling’ attacks. A whaling attack is a type of corporate phishing attack that targets high-level executives (CEO or CFO), to steal sensitive information from a company. In some instances, hackers may pose as the CEO or other executives to manipulate their targets into authorizing access to financial information or employees’ personal information. For that reason, organizations should consider investing in specific cyber security training for their high-level executives.
Key organizational cyber risk challenges
To have an effective and efficient cyber risk management process, there are several challenges that an organization has to address. The main challenges are:
Lack of visibility: a majority of security professionals are apprehensive about ransomware and phishing attacks. Limited visibility of such attacks and the burden of being flooded with alerts to act upon are further substantial concerns. The lack of visibility has triggered many challenges for businesses. For instance, how are you supposed to resist threats that you do not even know about? What businesses need are solutions that operationalize threat intelligence and provide real-time protection and several layers of security from recognized bad locations. Organizations must have access to solutions that can spot an array of cyber threats and that offer better visibility of risks pertinent to their industry.
Prioritizing cyber risks: handling growing cyber threats can be overwhelming. The possibility of a failure is well known, but businesses never seem to have a sufficient workforce or financial plan to manage it all in real-time. What needs to be done first? A proper risk prioritization plan needs to be in place to answer this question. A key driver in determining the priorities is to stay agile in the face of swiftly changing cyber threats, business conditions, company goals, and technology defenses.
Cyber risk prioritization has to be evaluated in a big-picture framework, tied to key business objectives, and considered against a credible danger-versus-resources assessment. Of course, that needs to be done at the top, possibly with substantial input from the board, and it must be conveyed clearly to all stakeholders.
Communicating cyber risks to the board and management: Chief Information Security Officers (CISO) often find it hard to express the significance of security to the top leadership and validate further investments for their endeavors, regardless of how crucial they are. It is difficult to instill the principles of security into the larger business model, even if they are key to reducing the risk of incidents.
The ability to show how security initiatives can help the business reduce time and costs on certain processes is an ideal way to show a department’s competence. It is particularly crucial when CISOs are asking for the allocation of more budget. To support the argument, it is recommended to have a metrics-heavy dialogue.
Sophisticated ransomware: ransomware attacks are rising, and business leaders and IT professionals need to have a robust recovery strategy against such attacks to protect their business. There have been several submissions about the advancement of ransomware and the wait-and-watch game between fraudsters who are seeking ways to get around detection abilities and guards looking for ways to thwart them. Rather than arbitrarily encrypting data, offenders are focusing on high-value business data to encrypt and hold to ransom.
The recent Digital Defense Report by Microsoft has taken a profound look into cybercrime trends, applying its expertise and insights into enterprise, server, desktop, and cloud networks. The report mentions ransomware as the most troublesome threat, and the most widespread reason behind its own incident response engagements.
Cloud risks: businesses are relocating their classified data to the cloud from legacy data centers, because of the cost and flexibility involved in legacy data centers. Shifting data to the cloud requires appropriate configuration and security procedures in place or else there is a possibility of businesses falling into a trap. Cloud service providers secure only their own platform. The responsibility of securing a firm’s infrastructure from theft and deletion on the cloud lies with the firm. Current incident response teams must have the necessary skills and tools to perform forensics on cloud data. Leaders must challenge their teams on their preparation and capability to supervise and act in response to security attacks in the cloud.
Staff and skills shortage: cyber risks today have become more sophisticated than ever, and this has triggered a steady pattern of relying too much on point products to shield against threats. While technology is key to this objective, it is not a standalone answer. Often, mid-market firms lack devoted cyber security personnel that are just as important. This skills shortage has been exacerbated by the pandemic as the network graph has broadened to include at-home laptops and other WFH access points. Hiring more security specialists together with outsourced professionals is the only way forward.
Perpetually evolving risks: the polymorphism particularly with respect to malware is something that you cannot do much about. Polymorphic malware is dangerous, damaging computer software such as a virus, worm, or spyware. It can change its form frequently, making it tough for anti-malware programs to identify it. That is why companies must consider adding an additional layer of protection, on top of antivirus tools.
Conclusions
Managing risk across the enterprise is harder than ever today. Modern security landscapes change frequently, and the explosion of third-party vendors, evolving technologies, and a continually expanding minefield of regulations challenge organizations. The COVID-19 pandemic and associated economic impacts have further raised the bar for security and compliance teams by creating more responsibility with diminishing resources.
Organizations need to protect the basic functions that allow the company to survive, grow and perform. These functions are the adaptability and stability mechanisms. One of the purposes of cyber security should be to protect these functions from cyber risks. Practitioners should consider identifying cyber threats that could harm the adaptability and stability functions in any type of organization.
To be able to adequately manage their cyber risks organizations need to have teams trained in each component of cyber risk management and the methodologies that support this: (1) Risk identification (2) Risk prioritization (3) Respond and (4) Assess/improve.
The organization has to identify a cyber risk management framework that best meets its information security needs.
Organizations should get involved in cyber security benchmarking, to be able to keep tabs on security efforts. Cyber security metrics need to be tracked.
Integration of cyber security organizational risk management processes is a must. Many organizational risks will have a cyber component to them. Cyber risk should therefore be integrated with the organizational approach to risk management.
Establishing a cyber security culture can influence risk-based decisions and create the perception that security is a benefit to the business rather than an obstacle. Although organizations work diligently to improve cyber security awareness, network defense and threat detection, the greatest protection may originate from an effective risk-based cyber security culture.
Cyber security is a team effort. Every organization has different needs, both from budget and compliance standpoints. Like every other aspect of cyber security, no ‘one size fits all’ resource for cyber security training exists. Finding the right fit for the organization can be difficult and time consuming, but is necessary.
Cyber threats are an increasing phenomenon in today’s digitalized and connected operating environment. The same technologies that have enabled business transformation also enable or create cybercrime. Cyber attacks or breaches can, in the worst case, be devastating to a company. That is why cyber security should have a high priority on the agendas of top management and boards.
Cyber security was previously seen as the concern of IT security professionals alone. This, however, is changing, due to the growing awareness among senior executives and others about cyber threats and their potentially devastating effects on businesses. Cyber security is increasingly becoming a top management and board-level concern – and should very much be so.
The author
Alberto G. Alexander, Ph.D, MBCI, International Consultant Dr. Alexander holds a Ph.D from The University of Kansas and a M.A from Northern Michigan University. He is the Managing Director of the international consulting and training firm Eficiencia Gerencial y Productividad, located in Lima, Perú. He is a Professor at The Graduate Business School, of ESAN University and a member of the Business Continuity Institute. Contact him at [email protected]
Bibliographical references
- Leirvik, Ryan. Understand, Manage, and Measure Cyber Risk. Apress. 2021.
- Antonucci, Domenic. The Cyber Risk Handbook. Wiley, 2017.
- Hodson, Christopher. Cyber Risk Management Kogan, 2019
- Evans, Ariel. Managing Cyber Risk. Routledge, 2019
- Alexander, Alberto Implementing Enterprise Risk Management Continuity Central, 2018
- Frohnhoefer, Ray. Pangilinan, Luis. Risk Assessment Framework: Successfully Navigating Uncertainty. 2019 PPC Group.
- Microsoft Digital Defense Report 2021